The Airdrop Data Problem — And How Verifiable Queries Fix It

Airdrops remain one of the most widely used mechanisms for distributing tokens, rewarding early users, and bootstrapping protocol communities. They are also one of the most consistently problematic. Nearly every major airdrop over the past few years has been followed by controversy: accusations of sybil farming, opaque eligibility criteria, snapshot manipulation, and perceived unfairness. The root cause of most of these problems is not the concept of airdrops itself, but rather the data infrastructure used to determine who qualifies.
Why Airdrops Keep Failing
The typical airdrop workflow looks like this: a team decides on eligibility criteria, takes a snapshot of onchain state at a specific block, runs scripts against the snapshot data to compute a list of qualifying addresses, and publishes a Merkle root that allows eligible addresses to claim tokens.
Problems with trust and data integrity exist at every stage of this process. The eligibility criteria are often announced after the snapshot is taken, which means the community has no way to verify that the criteria were not adjusted to favor or exclude specific groups after the fact. The snapshot itself is typically computed by the team's internal infrastructure using centralized indexing services, with no public proof that the data was complete or correct. The scripts that process the data are rarely open-sourced, and when they are, there is no way to verify that the published script is the one that was actually run.
The result is a system in which the community is asked to trust that the team ran honest computations on accurate data. In an ecosystem built on the premise of trustlessness, this is a significant gap.
The Sybil Problem is a Data Problem
Sybil attacks on airdrops are well-documented. Farmers create hundreds or thousands of wallets, execute minimal qualifying activity on each, and collect disproportionate allocations. Teams respond with increasingly complex filtering, such as minimum transaction counts, interaction diversity scores, timing analysis, and cluster detection algorithms.
But all of these filters are only as good as the data pipeline that feeds them. If the filtering logic runs on centralized infrastructure with no proof of correctness, there is no way for the community to verify that the filter was applied consistently and fairly. There is also no way to verify that the underlying data, such as the complete set of transactions for every wallet over a multi-month period, was accurately collected and not manipulated or selectively queried.
The deeper issue is that sybil detection requires sophisticated data analysis. It’s necessary to compute graph relationships between wallets, analyze timing patterns across thousands of transactions, and aggregate behavior across multiple contracts and potentially multiple chains. This is a data processing task that exceeds what onchain logic can handle, which means it necessarily happens offchain. The question is whether it happens in a verifiable way or an opaque one.
Making Airdrop Eligibility Verifiable with Proof of SQL
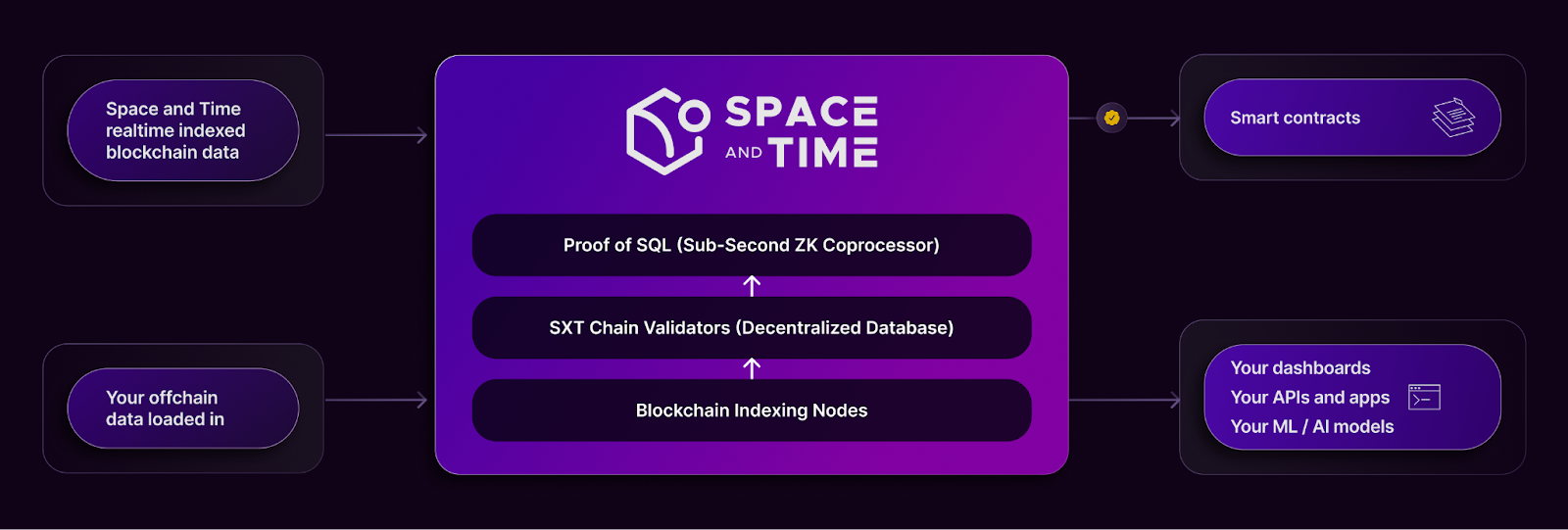
Space and Time offers a fundamentally different approach: instead of running eligibility computations in opaque, centralized pipelines, teams can define their eligibility criteria as SQL queries against SXT's indexed blockchain data, and every result is backed by a ZK proof generated by Proof of SQL.
SXT indexes the complete transaction history of major blockchains, from genesis block to the present, into relational tables. A team designing an airdrop can write SQL queries against these tables to define eligibility. For example, a query might select all wallets that interacted with a specific set of contracts at least N times, held a minimum balance for a certain number of blocks, and performed transactions on at least two different chains. This is a standard SQL query involving joins, aggregations, and filtering.
When this query is executed through Proof of SQL, the result comes with a ZK proof that attests to two things: the SQL computation was performed correctly, and the underlying data tables have not been tampered with. The data commitments referenced by the proof are signed by SXT's validator network through BFT consensus, meaning the data integrity is backed by cryptoeconomic security rather than trust in a single team.
What Changes for the Community
With this approach, the entire airdrop eligibility process becomes auditable and verifiable. The SQL query that defines eligibility can be published in advance, so the community knows exactly what criteria will be applied. The query is executed against tamperproof blockchain data indexed by a decentralized network, rather than a proprietary database controlled by the airdrop team. The result is accompanied by a ZK proof that anyone can verify, confirming that the published query was the one that was actually executed and that the data was not manipulated.
This eliminates the most common sources of airdrop controversy. The criteria are transparent. The data is verifiable. The computation is proven. There is no black-box script, no trust-me snapshot, and no room for selective filtering that cannot be detected.
Beyond Eligibility: Onchain Claim Verification
The benefits extend beyond eligibility computation. The ZK proof generated by Proof of SQL can be verified onchain by a smart contract, which means the claim process itself can be trustless. Instead of publishing a Merkle tree and asking users to trust that it was generated correctly, a protocol can have its claim contract verify the Proof of SQL output directly. The smart contract checks the ZK proof, confirms that the claiming address appears in the verified result set, and processes the claim.
This model also supports more dynamic and fair distribution mechanisms. Because SXT provides real-time data access, eligibility does not need to be frozen at a single snapshot block. Protocols can implement rolling eligibility windows, cumulative activity scoring, or multi-phase distributions wherein each phase's criteria can build on verified data from the previous phase.
A Higher Standard for Token Distribution
Airdrops play a major role in shaping user trust in a protocol. When that experience is marred by opaque criteria, sybil farming, and perceived unfairness, it damages trust before the protocol has had a chance to demonstrate its value. Verifiable query infrastructure raises the standard for how token distributions are designed and executed.
The technology to make airdrops provably fair already exists. Proof of SQL turns eligibility criteria from opaque scripts into transparent, verifiable computations. For protocols that want their airdrop to build trust rather than erode it, this is the infrastructure to build on.

